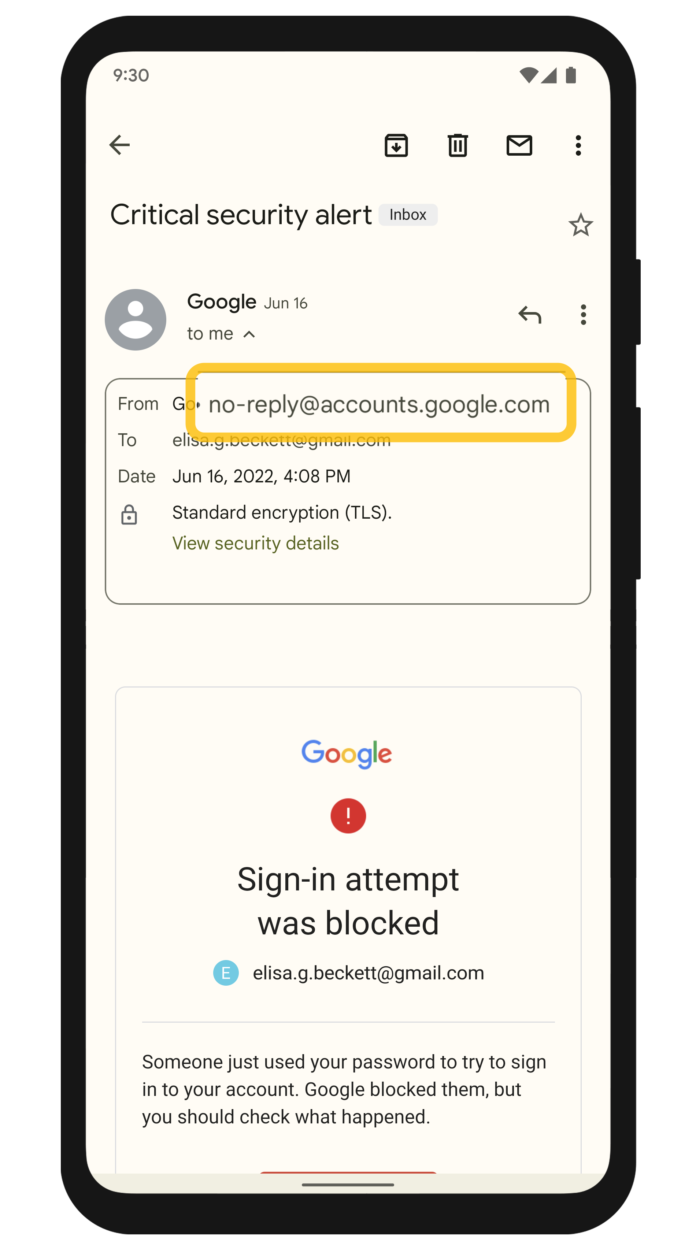
A new phishing scam is making waves and it’s more convincing than most. This time, the fake emails are actually signed by Google, passing Gmail’s security checks and appearing to come from a legitimate source.
The email, sent from no-reply@accounts.google.com, raises no red flags in Gmail. It directs recipients to a fake support page built using a Google service, tricking users into clicking links like “view case” or “upload additional documents.” These links then lead to a fake sign-in page a setup designed to steal login credentials.
Developer Nick Johnson, who first spotted the attack, explained that the hackers created a Google account tied to a registered domain, then built an OAuth app using the full phishing email as the app name. By giving this app access through their Google account, they triggered a real security notification email from Google which was then forwarded to targets, making it seem trustworthy.
The scam exploits two specific vulnerabilities:
1. The ability to embed scripts and arbitrary content on user-created websites.
2. The misleading use of Google’s authentication signature, even though the original email came from a third-party domain.
Initially, the bug report was closed with the claim that the behavior was intentional. However, after further review, Google has now committed to fixing the issue.
This is just the latest in a long string of sophisticated phishing campaigns using real tools to deceive users. It’s a stark reminder: even emails that look official should be handled with caution.
For more tech updates, visit DC Brief.